De #RDW stuurt mij een brief (op papier!) dat mijn auto een #APK nodig heeft. Is vorige week al gedaan, maar kennelijk zijn daar weer een paar systemen niet op elkaar aangesloten. Jammer. #verspilling
#apk
Newly Registered Domains Distributing SpyNote Malware
Cybercriminals are employing deceptive websites on newly registered domains to distribute AndroidOS SpyNote malware. These sites imitate the Google Chrome install page on the Google Play Store, tricking users into downloading SpyNote, a powerful Android remote access trojan. SpyNote is used for surveillance, data exfiltration, and remote control of infected devices. The investigation uncovered multiple domains, IP addresses, and APK files associated with this campaign. The malware utilizes various C2 endpoints for communication and data exfiltration, with functions designed to retrieve and manipulate device information, contacts, SMS, and applications.
Pulse ID: 67feb504b76dd387be73309b
Pulse Link: https://otx.alienvault.com/pulse/67feb504b76dd387be73309b
Pulse Author: AlienVault
Created: 2025-04-15 19:35:32
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Detailed Analysis of DocSwap Malware Disguised as Security Document Viewer
A new malware called DocSwap, disguised as a document viewing authentication app, was discovered targeting South Korean mobile users. The malware, linked to a North Korean APT group, performs keylogging and information theft through accessibility services. It decrypts an obfuscated APK file, executes code from a DEX file, and communicates with a C2 server to receive malicious commands. The malware requests extensive permissions, maintains persistence, and performs various malicious activities including camera manipulation and audio recording. The C2 infrastructure initially displayed a phishing page impersonating CoinSwap, later showing characteristics associated with the Kimsuky group. The threat actor has been designated as puNK-004 by S2W TALON.
Pulse ID: 67faa88ecf8cad21f1b6a246
Pulse Link: https://otx.alienvault.com/pulse/67faa88ecf8cad21f1b6a246
Pulse Author: AlienVault
Created: 2025-04-12 17:53:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Newly Registered Domains Distributing SpyNote Malware
Deceptive websites hosted on newly registered domains are being used to deliver AndroidOS SpyNote malware, mimicking the Google Chrome install page on the Google Play Store. The campaign utilizes a mix of English and Chinese-language delivery sites, with Chinese-language comments in the code. The malware is distributed through a two-stage installation process, using an APK dropper to deploy the core SpyNote RAT. SpyNote is a potent Android remote access trojan capable of extensive surveillance, data exfiltration, and remote control. It aggressively requests numerous intrusive permissions, allowing for theft of sensitive data and significant remote access capabilities. The malware's keylogging functionality and ability to manipulate calls, activate cameras and microphones, and remotely wipe data make it a formidable tool for espionage and cybercrime.
Pulse ID: 67f80a4aa4c9d5d796071af6
Pulse Link: https://otx.alienvault.com/pulse/67f80a4aa4c9d5d796071af6
Pulse Author: AlienVault
Created: 2025-04-10 18:13:30
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Bonjour besoin d'aide pour une #apk enfants je cherche Play Doh touch ou une autre application qui ferait la même chose sachant que le Play Doh touch pour Android ne se trouve plus sur l'App store quelqu'un aurait une idée où le trouver svp ?
Beware! Fake 'NextGen mParivahan' Malware Returns
A new variant of the fake NextGen mParivahan malware has emerged, exhibiting enhanced stealth and data theft capabilities. The malware, disguised as a government traffic notification system, tricks users into downloading a malicious app that requests extensive permissions. This latest version targets messages from social media, communication, and e-commerce apps, posing a greater threat to user privacy. It employs advanced techniques such as malformed APKs, multi-stage dropper-payload architectures, and dynamic C2 generation to evade detection. The malware steals sensitive data, including SMS messages and notification content, uploading it to Firebase or a C2 server. Its ability to access notifications, SMS, and app data significantly risks user privacy, highlighting the need for improved security awareness and analysis tools.
Pulse ID: 67f6b1c771e854bfa88f7cfd
Pulse Link: https://otx.alienvault.com/pulse/67f6b1c771e854bfa88f7cfd
Pulse Author: AlienVault
Created: 2025-04-09 17:43:35
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Analysis of New Mobile Banking Malware
Salvador Stealer is a newly discovered Android malware that poses as a banking application to steal sensitive user information. It employs a multi-stage attack chain, utilizing a dropper APK to install the main payload. The malware incorporates a phishing website within the app to collect personal and banking data, including Aadhaar numbers, PAN card details, and net banking credentials. It exfiltrates stolen information in real-time to both a phishing server and a Telegram-based Command and Control server. Salvador Stealer also intercepts SMS messages to capture one-time passwords and banking verification codes, bypassing two-factor authentication. The malware demonstrates persistence mechanisms, automatically restarting itself if stopped and surviving device reboots. Analysis revealed exposed infrastructure, including an accessible admin panel, potentially linking the attacker to India.
Pulse ID: 67ec5957bfba1cac452b1059
Pulse Link: https://otx.alienvault.com/pulse/67ec5957bfba1cac452b1059
Pulse Author: AlienVault
Created: 2025-04-01 21:23:35
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

APK Explorer & Editor, an open-source tool to explore the contents of an installed #APK, is strictly made with an aim to inspect an installed APK file.
https://f-droid.org/packages/com.apk.editor
https://github.com/apk-editor/APK-Explorer-Editor
#android

#Android #AndroidUygulamaları #apk #APKDL #APKİ...
https://www.dblogum.net/list/guvenli-apk-indirebileceginiz-web-siteleri/
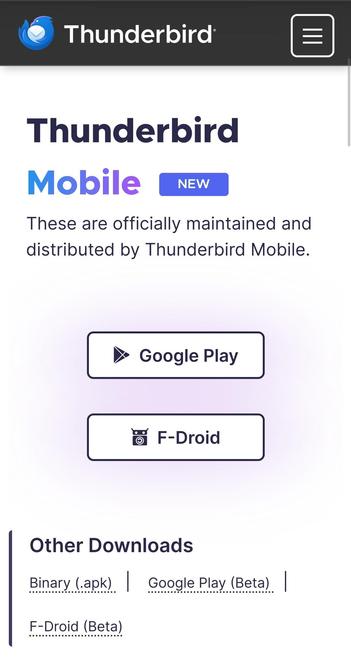
Do you love Thunderbird on your PC? Remember a mobile version is now available for Android users (Play Store, F-droid and apk file): https://www.thunderbird.net/download/. And it works really well! #Thunderbird #OpenSource #Windows #MacOS #FOSS #Linux #Mozilla #PlayStore #apk
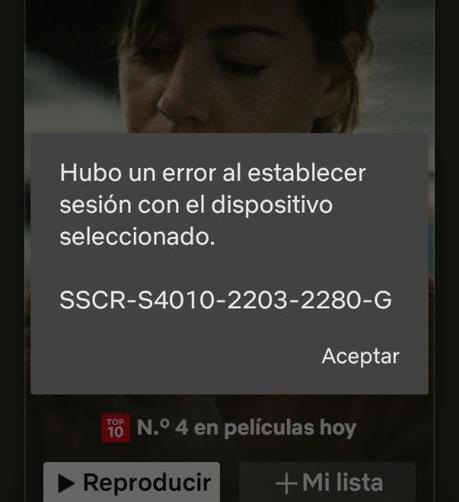
Chromecast (2da generación, etc) : Cómo solucionarlo desde la comunidad de software libre.
La solución (no oficial y de la comunidad de software libre) lleva disponible cuatro días; solo necesitas saber cómo implementarla con este tutorial.
También incluye instrucciones para reparar un dispositivo que se restableció a la configuración de fábrica.
#chromecast #howto #YuriyMysochenko & #MaciejMensfeld #apk #ActivityManager #android #fdroid #SoftwareLibre
http://drcalambre.blogspot.com/2025/03/como-corregir-el-error-del-9-de-marzo.html
Yuriy Mysochenko: Activity Manager Developer
@aldi80s The solution (unofficial and from the free software community) has been around for four days, you just need to know how to implement it with this tutorial.
It also includes instructions on how to "fix" one that went through the factory reset procedure.
#chromecast (how to fix it from free software community)
#YuriyMysochenko & #MaciejMensfeld #apk #ActivityManager #android #fdroid #freesoftware

https://www.wacoca.com/games/1092932/ Temple Run – Gameplay Walkthrough Part 12 – New 2025 Update (iOS, Android) #ads #apk #app #download #FreeGames #hack #MobileGames #MOD #tapgameplay #TempleRun #TempleRunAndroid #TempleRunGame #TempleRunGameplay #TempleRunIos #TempleRunTutorial #trailer #walkthrough #スマホゲームアプリ #無料のスマホゲームアプリ
Spotify bloquea definitivamente las APK piratas: usuarios no pueden acceder a sus cuentas premium “gratuitas” https://blog.elhacker.net/2025/03/spotify-bloquea-apk-pirata-cuentas-premium.html #android #spotify #apk #app

Not completely true. I'm guessing there is no Android app on the Google Play Store
play.google.com/store/apps/developer?id=Daniel+Supernault&hl=nl
but there sure is an apk you can try on GitHub released by the main developer himself @dansup
https://github.com/joinloops/loops-app/releases/tag/v1.0.0.13
If you want you can test it out and let me know if it worked
@Morpurgo It's explained here : https://wiki.obtainium.imranr.dev #obtanium #android #apk
احصل على تجربة سينمائية مميزة مع تطبيق سينما توب Cinema Top APK آخر إصدار لعام 2025!
استمتع بمشاهدة أحدث الأفلام والمسلسلات بجودة عالية وواجهة مستخدم سهلة الاستخدام. لا تفوت الفرصة، حمله الآن وابدأ المتعة!
#سينما_توب #APK #أفلام #2025
We're starting to implement support for split APKs in #FDroid. #Google wants to gather as much data about its users as possible, so trying to hide info about language, country, device specs was not a design concern for them. It is central for us. We want the official client to leak as little data as possible to any server, be it ours, mirrors, or custom repos. We welcome input:

R8: Шакалья работа (уменьшение apk через правки R8)
По умолчанию для минификации имени класса в R8 используются цифры и английский алфавит. Но что будет если вместо трех символьных строк, которые будет занимать три байта, использовать один двухбайтовый символ?