Apache Tomcat: CVE-2025-24813: Active Exploitation
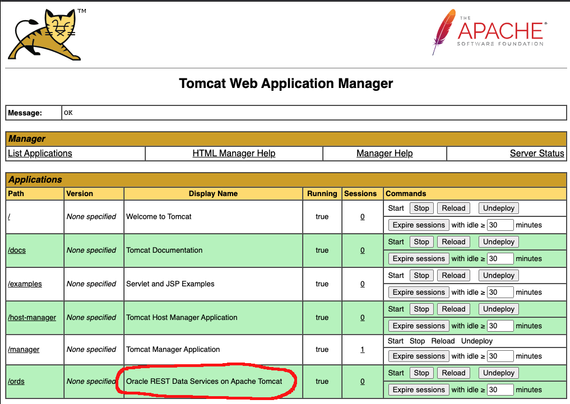
A critical path equivalence vulnerability in Apache Tomcat, CVE-2025-24813, allows unauthenticated attackers to execute arbitrary code on vulnerable servers under specific conditions. The vulnerability affects Tomcat versions 11.0.0-M1 to 11.0.2, 10.1.0-M1 to 10.1.34, 9.0.0.M1 to 9.0.98, and certain 8.5.x versions. Exploitation requires specific server configurations and involves sending malicious PUT and GET requests. Six malicious IP addresses have been identified attempting to exploit this vulnerability, targeting systems in the US, Japan, Mexico, South Korea, and Australia. Multiple proof-of-concept exploits have been published, increasing the likelihood of ongoing exploitation attempts. Users are advised to upgrade to patched versions or implement network-level controls to restrict access to the Tomcat server.
Pulse ID: 67e6c6b6dd57e4c62a1a8d1f
Pulse Link: https://otx.alienvault.com/pulse/67e6c6b6dd57e4c62a1a8d1f
Pulse Author: AlienVault
Created: 2025-03-28 15:56:38
Be advised, this data is unverified and should be considered preliminary. Always do further verification.