4:02am I See the Light by Cracker from Cracker
#KJAC #TheColoradoSound #Cracker
#cracker
Resteverwertung der leckeren Art
https://friendica.world/display/84b6ef2b-1967-d1eb-74e8-27d604479904
5:34am I See the Light by Cracker
#KJAC #TheColoradoSound #Cracker
4:57am King of Bakersfield by Cracker from Berkeley to Bakersfield
#KJAC #TheColoradoSound #Cracker
4:22pm King of Bakersfield by Cracker
#KJAC #TheColoradoSound #Cracker
9:06pm Happy Birthday by Cracker from Cracker
#KJAC #TheColoradoSound #Cracker
Are you an aspiring safe-cracker . . .? Then have I got a deal for you Practice in the comfort of your own garage until you’re ready to step up to the big time Note – the safe has no key. Pick up in #Thornbury #cracker #BigTime #Raffles
4:28am Another Song About the Rain by Cracker
#KJAC #TheColoradoSound #Cracker
So, heute habe ich unseren #PV Strom mal ausgiebig selbst genutzt.
#Sauerteig #Brot #Sauerteigreste #Cracker und eine Premiere, mein erstes, selbstgemachtes Knusper#Müsli.
Cracker Barrel Thanksgiving menu is out. Here’s when you can order https://www.diningandcooking.com/1910193/cracker-barrel-thanksgiving-menu-is-out-heres-when-you-can-order/ #Barrel #Connect #country #Cracker #CrackerBarrelOldCountryStore #local #LocalConnect #Modular #ModularStory #old #point #store #story #thanksgiving #ThanksgivingAppetizes #ThanksgivingDesserts #ThanksgivingFood #ThanksgivingRecipes #ThanksgivingSides #the #to #ToThePoint
Spicy Sellerie-Nuggets in einer Panade aus Salzcrackern und Cheddar mit asiatischem Wirsing
@nixCraft
#hacker originally I read were from MIT who used to sneak in and work on the model trains and their control systems; later a term for computer enthusiast who would find security issues in software generally for good motives (white, grey hats).
#cracker a hacker who looks to break into computer systems for illicit reasons (black hat), not for exploration & understanding, but profit or destruction.
There is no backdoor that's only for the good guys. If you create a backdoor, it's not just your backdoor, it's everyone's backdoor, and believe me, people WILL find it, and exploit it, they will.
The image at the top of this blog is, from what I can find, the first stock image photo of a hacker in a ski mask that ever appeared in print, carrying on a visual association between hackers and bank robbers or safe crackers that has continued since 1969.
How tropes and stereotypes originated and became perpetuated in the media is one of the main focuses of the realhackhistory project.
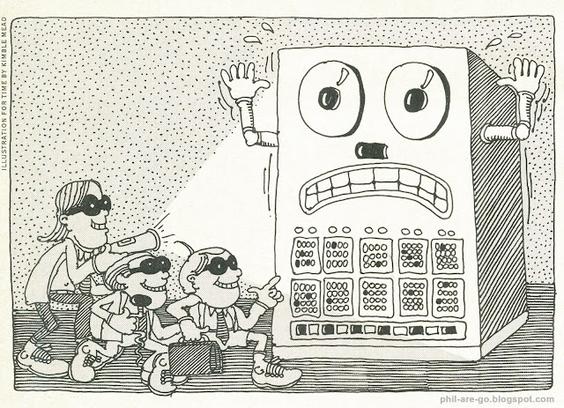
Illustration from “Superzapping in Computer Land”, TIME Magazine, January 12th, 1981We can be almost certain of being wrong about the future, if we are wrong about the past.
Gilbert K. Chesterton
Before I try to define what this website and the associated YouTube and Mastodon accounts are all about I want to discuss what they aren’t.
This history research, documentation and analysis project is not about trying to dox hackers from the past, reveal secrets that could get people into legal peril or fuel hacking scene gossip. I’m not interested in when Java was invented or the anniversary of the first web browser being created here either though, we are talking about hackers. The ‘darkside’.
This project is about documenting the history of people like Neal Patrick in the video below, who became the face of hacking in 1983 after being raided by the authorities, along with his hacking group the 414s.
https://www.youtube.com/watch?v=dA3NuQdhu5U
Behind the blogs, the YouTube videos, FOIA documents, clips of funny hacker related TV shows or movies and the memes, realhackhistory is a genuine desire to keep the knowledge and stories of hackers of the past alive and provide some lessons that can still help people interested in hacking today.
I envision realhackhistory as a trail of breadcrumbs to help get you started on your way to understanding the past, and hopefully the present, of hacking better. Think of this as digital archaeology, if it makes it all sound cooler.
Information on the Internet is frequently wrong
If we start with some basic questions such as “what was the first computer virus?” or “when was the first denial of service attack?” and plug them into your search engine of choice you’ll start to notice something.
It isn’t that there are conflicting answers, some of these questions hinge on a subjective understanding of details such as what defines a computer virus, what operating system did it function on, what language was it coded in, etc. No, you start to notice how many answers that are clearly wrong are stated emphatically as fact.
We need an example, right? Let’s analyse this text below, from the online version of Encyclopedia Britannica:
The first documented DoS-style attack occurred during the week of February 7, 2000, when “mafiaboy,” a 15-year-old Canadian hacker, orchestrated a series of DoS attacks against several e-commerce sites, including Amazon and eBay.
Encyclopedia Britannica, “denial of service attack” entry
Let’s unpack this. While it is true that mafiaboy carried out a widely reported on campaign of distributed denial of service (DDoS) attacks against high profile websites in 2000. This was not the first distributed denial of service attack and definitely not the first denial of service attack either.
Mafiaboy, an aficionado, but not originator, of denial of service attacksDistributed denial of service attacks, called “Net Strikes” by participants, were organised by hacktivists in the mid 90’s against French government websites which involved getting people to manually refresh those websites at a set time. There was also a huge DDoS attack against Manhattan based ISP Panix in September of 1996.
The first denial of service attack over a computer network is widely believed to have been in 1974, when someone discovered a way to use a newly introduced feature in TUTOR to lock up other PLATO terminals remotely at CERL, the Computer-based Education Research Laboratory, at the University of Illinois Urbana-Champaign.
It doesn’t necessarily matter that there may have been other denial of service attacks before 1974, what matters I think is that the first denial of service attack was definitely not in 2000 and that this is incorrect information being presented as fact.
How did this clearly wrong history sneak into an encyclopedia? I would suspect the loop of incorrect information that begins to be circulated online and eventually becomes, through copying, regurgitation and repetition, accepted fact. Nobody bothers to go back to original sources, lazy journalism becomes grist for a slew of blogs which eventually becomes part of a reference book and then accepted fact.
Incorporating AI into search engines will only make this problem worse, if the average of all the information about the history of hacking is a bunch of copypasta in infosec marketing or lazy journalism then that is what the AI search function will regurgitate. Garbage in, garbage out.
Tracing attitudes to hackers in pop culture
Hackers were not always demonised, hacking was not always a part of pop culture and the word “hacker” itself was not widely used to describe anything other than a bad golfer until mid 1983. I’ve written a whole blog on the topic.
The ‘Whiz Kids’, from the 1983 TV show of the same name about teens who solve mysteries with the aid of computers, social engineering and hackingWe can look at how journalists wrote about hacking and hackers in the past and how hackers evolved as character archetypes and hacking became a trope in movies and television.
We can chart the way hackers are viewed, from novelty or curiosity through to menace and then back to heroic anti-heroes before lately becoming a facet of shadowy criminal gangs, as the view of hackers as professionalised “cybercriminals” takes hold in the public imagination.
The German poster for 1983’s WarGames, a movie about hacking in which the word “hacker” is never usedThe 90’s saw an explosion of hacker and hacking related movies as people became unable to ignore the rise of the internet and computers became a part of every day life. I made a YouTube video about one such movie, The Net.
https://www.youtube.com/watch?v=ug3-h7nYV0Q
Hacker related documentaries, news segments and TV specials created by non-hackers provide a fascinating snapshot of the attitudes towards hackers and how hacking touched on current events at the time the documentary was filmed. I’ve put as many as I can find from over the years up on my YouTube channel.
Preserving & promoting hacker culture
While a lot of people have heard of 2600 Magazine, or the phrack e-zine, there is a lot more hacker culture created by hackers themselves out there waiting to be discovered.
Take published books about hacking written by hackers for instance, in the UK there was various editions of Hugo Cornwall’s book “The Hacker’s Handbook”, originally published in 1985. There was also infamous subversive publisher Loompanic’s book “The Computer Underground: Computer Hacking, Crashing, Pirating, and Phreaking” by M. Harry, which was also published in 1985.
- “The Hacker’s Handbook”, original 1985 edition, by Hugo Cornwall
- “The Computer Underground: Computer Hacking, Crashing, Pirating, and Phreaking” by M. Harry, Loompanics, 1985
Reading these books not only give us a snapshot of the scene at the time through the author’s eyes, but also a chance to read how hackers themselves defined a hacker.
This book uses the word in a more restricted sense: hacking is a recreational and educational sport. It consists of attempting to make unauthorised entry into computers and to explore what is there. The sport’s aims and purposes have been widely misunderstood; most hackers are not interested in perpetrating massive frauds, modifying their personal banking, taxation and employee records, or inducing one world super-power into inadvertently commencing Armageddon in the mistaken belief that another super-power is about to attack it.
Every hacker I have ever come across has been quite clear about where the fun lies: it is in developing an understanding of a system and finally producing the skills and tools to defeat it. In the vast majority of cases, the process of ‘getting in’ is much more satisfying than what is discovered in the protected computer files.
“The Hacker’s Handbook” – Introduction, Hugo Cornwall, 1985
Documentaries about hackers by hackers or people affiliated with the hacking scene are a more vivid look at some of the personalities who shaped scene history, or notable events that took place. Annaliza Savage’s “Unauthorized Access” released in 1994 is required viewing, as is “Hackers 95” by Phon-E and R.F. Burns, released in 1995 (of course), you can see a short clip of below.
https://youtu.be/7abDgYYXhks?si=8upHxOHKs8wB6jX2
Over at textfiles.com you can find an incredible resource in the form of archived hacker scene text files, from the BBS years up to the era of the world wide web. Among the files archived is a great many hacker e-zines, or electronic magazines, text and text ASCII art documents that were published on a regular or semi-regular schedule.
The most famous hacker e-zine is undeniably phrack magazine.
Basically, we are a group of phile writers
who have combined our philes and are distributing them in a group. This newsletter-type project is home-based at Metal Shop… These philes may include articles on telcom (phreaking/hacking), anarchy (guns and death & destruction) or kracking. Other topics will be allowed also to an certain extent.phrack issue #1, Taran King, November 17th, 1985
Hacker media is also in print though, with magazines like the now defunct Technological American Party Magazine of the 1970s or Blacklisted! 411 back in the nineties or 2600, which is still going strong.
2600 Magazine issue 1, page 6, January 19842600 Magazine began in January of 1984 with an article discussing a criminal case that contributors to the magazine had been involved in the year before the first issue came out. It was a series of raids on young hackers across the U.S. that the FBI called “Operation Mainframe”. I created a video on one of the groups caught up in the FBI investigation, the Inner Circle.
https://www.youtube.com/watch?v=ppbx2POxxZU
2600 staff continued to be involved in hacking related incidents in the years after, as we can see from the article from 1985 below that notes that the editor of 2600 had his BBS seized by New Jersey police.
“Police hunt suspects” – Altus Times, 18th July, 1985You can find scanned issues of publications like Blacklisted! 411 over at archive.org and you can subscribe to 2600 over at their website.
Freedom of Information Act requests
Locked away in dusty archives is a wealth of information on the history of hacking, specific hackers and hacking groups, held by government bodies and law enforcement agencies.
To paraphrase NatSecGeek, if you are willing to take five minutes to write a FOIA request and then to wait potentially years for that request to be fulfilled you can eventually find yourself with documents that can rewrite our understanding of events in the history of hacking. My inspiration for pursuing FOIA requests as part of realhackhistory has been the aforementioned NatSecGeek as well as hexadecim8 and their Hacking History project.
You can find the documents they have retrieved from various archives here, and you can find my uploads of responsive records over at archive.org.
If requesting FOIA documents can be a bit boring and laborious, receiving them makes me feel like a little kid on Christmas morning.
FOIA archive requests can turn up completely different versions of events that had long been considered to be definitively settled. Records can show us scans or photocopies of newspaper or magazine articles since lost to time, printouts of webpages that are no longer online and the chance to see how government agencies or law enforcement have viewed the computer underground over the years.
In requesting documents I have primarily focused on records relating to hacking incidents between 1980 and 2005, with a particular interest in records from the early to mid 1980’s as records can degrade or get lost over time.
Because of FOIA requests we can see that in 1983 some people were so upset about the FBI raiding high-school age hackers linked to the Inner Circle hacking group that they wrote their Senator in California.
Or we can see the actual photocopies of notes of targeted systems seized by the FBI from those same hackers.
The text files, e-zine and magazine articles written by hackers provide one part of the story, the newspaper articles and TV segments on hacking incidents provide another and FOIA documents are the last piece of the puzzle that we as hacker history enthusiasts can hope to get our hands on in terms of records.
I plan future blog entries on how to file FOIA requests, how to decide what to FOIA and some dead ends I have reached in relation to past hacker events and incidents that someone else might want to pick up the threads from.
In conclusion
So that’s it, an explanation as to why realhackhistory exists, long since overdue and the start of a call to action for others who are interested, to see what they can add to the public knowledge of the roots of the hacking scene.
If I can outline a roadmap for the future of the project, I want to expand my understanding of the history of hacking outside of the English speaking world, start finding countries outside of the U.S, the U.K. and Australia to FOIA and pursue freeing more media from closed archives.
I’d also like to take this time to thank the people who have inspired me along the way, in particular Gabriella Coleman, Emma Best and Emily Crose, for encouragement and guidance on this great journey.
If we don’t preserve our history, nobody else will.
#1 #1980s #BBS #computer #cracker #crackers #cracking #darkSide #darkside #DDoS #encyclopedia #FBI #films #FOIA #hacked #hacker #hackers #hacking #historical #history #InnerCircle #IRC #mafiaboy #media #Movies #newspaper #police #television #TV #underground #WarGames
#HappyBirthday @carolynmccormick_official #carolynmccormick #actress #minuet #startrek #thenextgeneration #spencerforhire #lawanorder #trialbyjury #CriminalIntent #cracker #judgingamy #onelifetolive #bull #aholidayspectacular #thepost #mapplethorpe #thelastthingmarysaw #startrek58 @startrek @startrekonpplus @streammaxla
Spicy Sellerie-Nuggets in einer Panade aus Salzcrackern und Cheddar mit asiatischem Wirsing